Make Meraki Run Dns Tests Again
What you need to know to get your Cisco Meraki AP running.
With its sleek packaging and clean lines, receiving Cisco Meraki gear in the post can be exciting and thrilling — 1 thing it doesn't have to exist is daunting.
In fact, nosotros sat a friend, not a Meraki employee, down with nil more than this guide, a laptop, and a Cisco Meraki access point to come across how long it would take someone with lilliputian to no networking experience to fully gear up their ain wireless network. The upshot? A simple wireless network, setup in xxx minutes. Run into for yourself…
GETTING STARTED
Creating a Cisco Meraki dashboard
Earlier opening the box or plugging in the device, y'all'll demand to create your own Meraki dashboard account at dashboard.meraki.com past selecting Create an account and filling out some basic information. The Cisco Meraki dashboard is non an appliance, just a cloud-based service providing unified direction of all Cisco Meraki devices, constantly monitoring, optimizing, and reporting on your network.
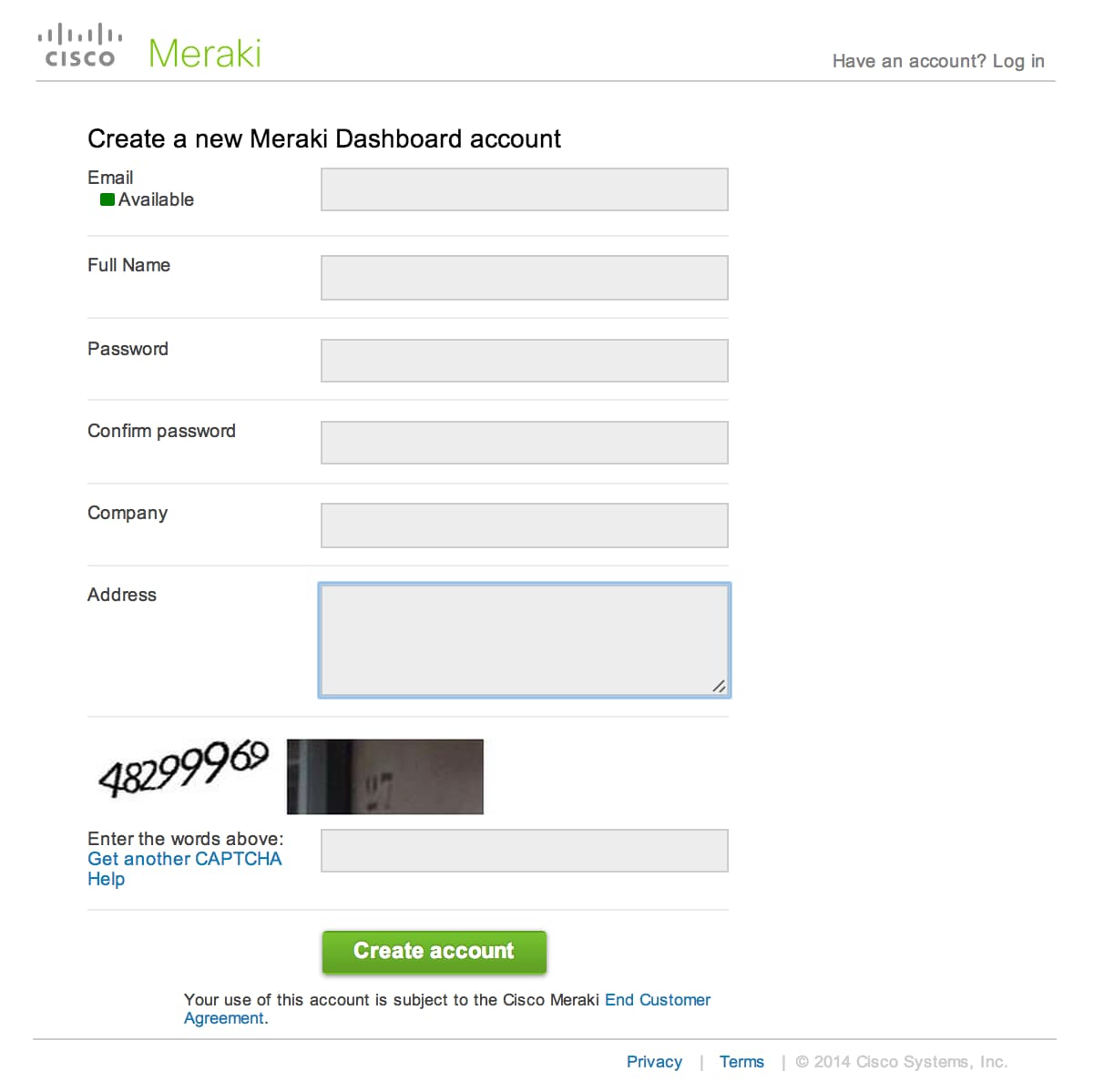
Calculation devices to dashboard
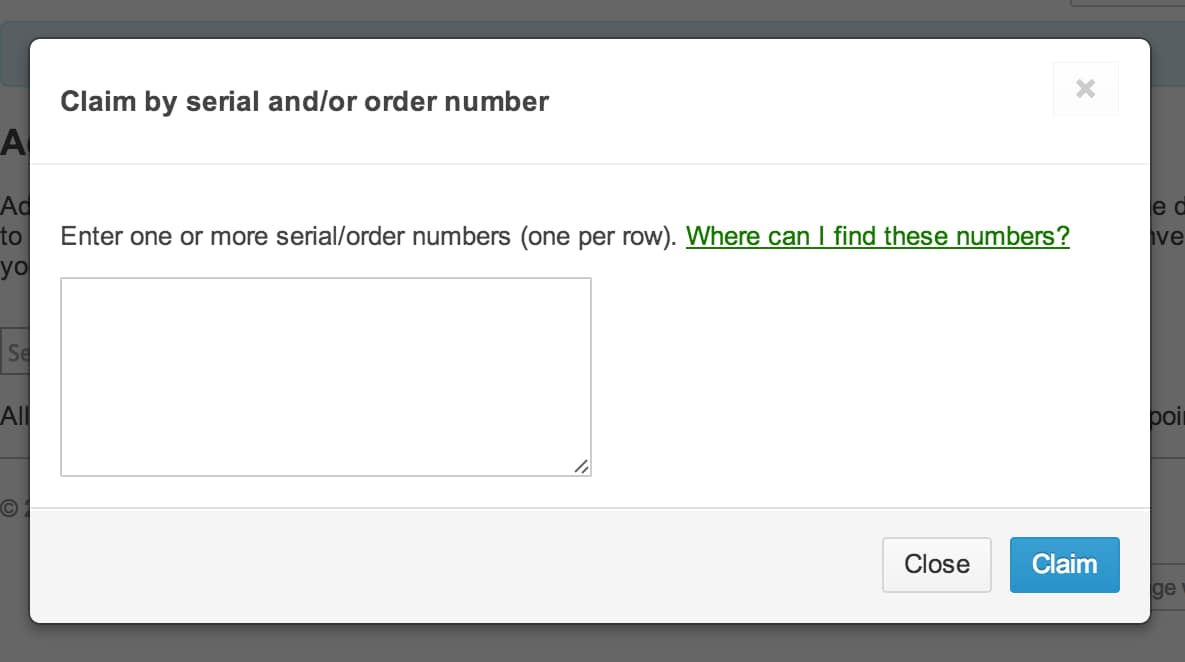
The next screen gives the option to add devices past providing the device's serial number or the order number. If you take multiple devices, entering the purchase order number will propagate the dashboard with all the devices in that order. If you already have a dashboard account created or have advanced past this prompt, you can also add devices by navigating to Configure > Add devices, clicking Claim, and again entering either the serial number or the gild number.
BASIC CONFIGURATIONS
At present that the devices accept been added to the dashboard, it'south time to make a few initial configurations. These will ensure proper advice from your access point to the Internet and the Cisco Meraki cloud, provide admin access to authorized users, and allow effective management and reporting capabilities.
Obtaining an IP address
Sometimes it's necessary to brand changes in order to connect to the Internet. When connected to a Meraki AP or straight downstream from one, my.meraki.com provides local configurations for Cisco Meraki access points. Hither admins tin can perform bones troubleshooting and set static IP addresses for uplink interfaces (It's also possible to gear up a static IP address from dashboard if needed).
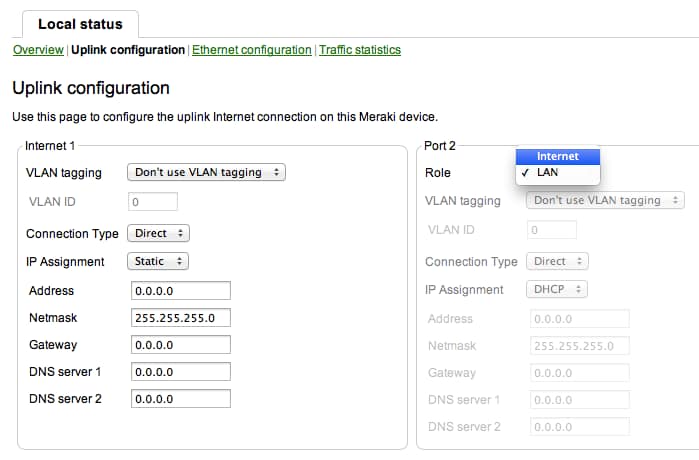
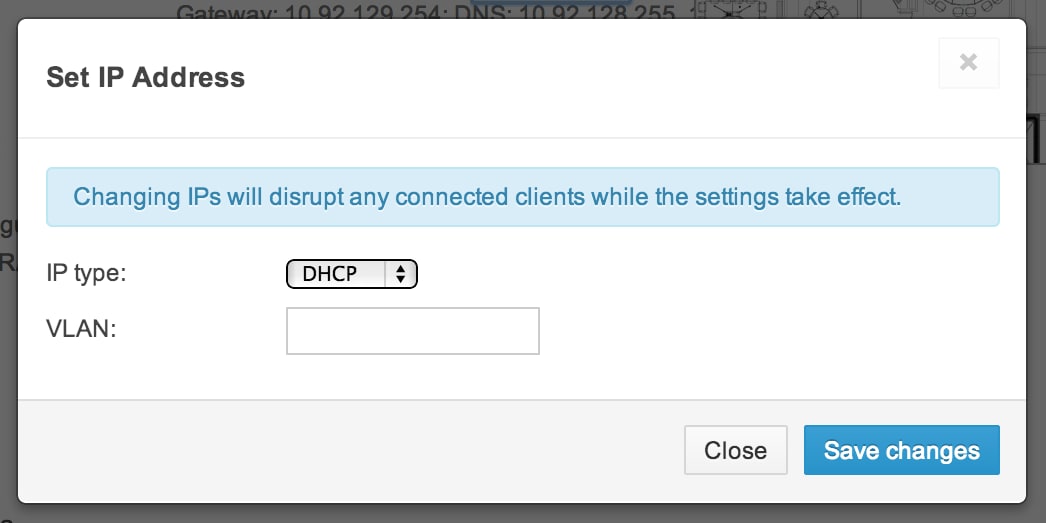
Cisco Meraki APs are set up to use DHCP out of the box. By clicking into an AP from the the Monitor > Access points folio, IP address information is available and can be changed by clicking ready IP address.
Opening firewall ports for dashboard admission
The next pace is to ensure that the proper protocols and ports are permitted on the firewall side to allow secure communication to the dashboard. If a firewall or gateway exists in the data path between Cisco Meraki devices and the cloud-managed dashboard, advice will be hampered until these configuration changes are made.
Adding admins for function-based dashboard access
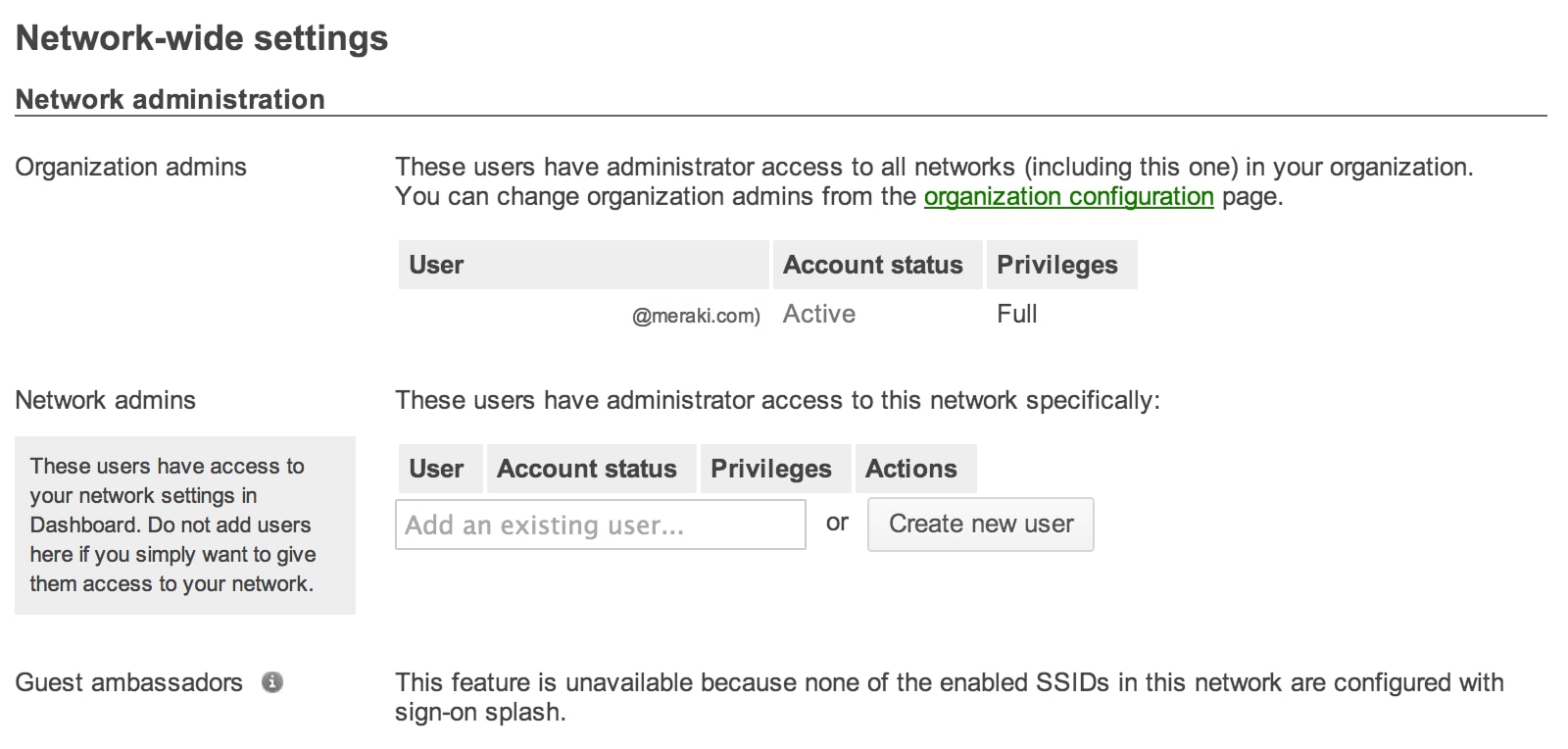
It's typical that more than 1 person will serve as a network admin and will therefore need admission to all or certain parts of dashboard. There are various levels of dashboard access to choose from and by navigating to Configure > Network-wide settings, it's simple to add new admins under the Network administration section, customizing what they tin can command and view. A further roll downwards on the same page, to the Network alerts department, provides the option to transport various alerts to all admins or simply certain ones.
PLUG AND PLAY
With the basic setup completed in dashboard, information technology's at present time to unbox, plug in, and start using that new AP.
Booting up the AP
Included in the box is mounting hardware for installing the AP in an optimal location. However, before mounting information technology high on a wall, information technology needs to be plugged in and accept the above configured dashboard settings downloaded. This process just entails plugging a CAT5 Ethernet cablevision into the AP's uplink connector. If powering the device via a PoE enabled switch port or PoE injector, that'southward all there is to it. Otherwise an A/C adapter volition exist needed.
Once plugged in, the AP will automatically attempt to connect to the dashboard to download its configurations and run a self-diagnostic. During this time, the LED light on the device will provide a colorful low-cal evidence, ultimately settling on solid greenish or solid blueish calorie-free (depending on whether clients are associated) if connected properly.
Adding APs to the map or a floor program
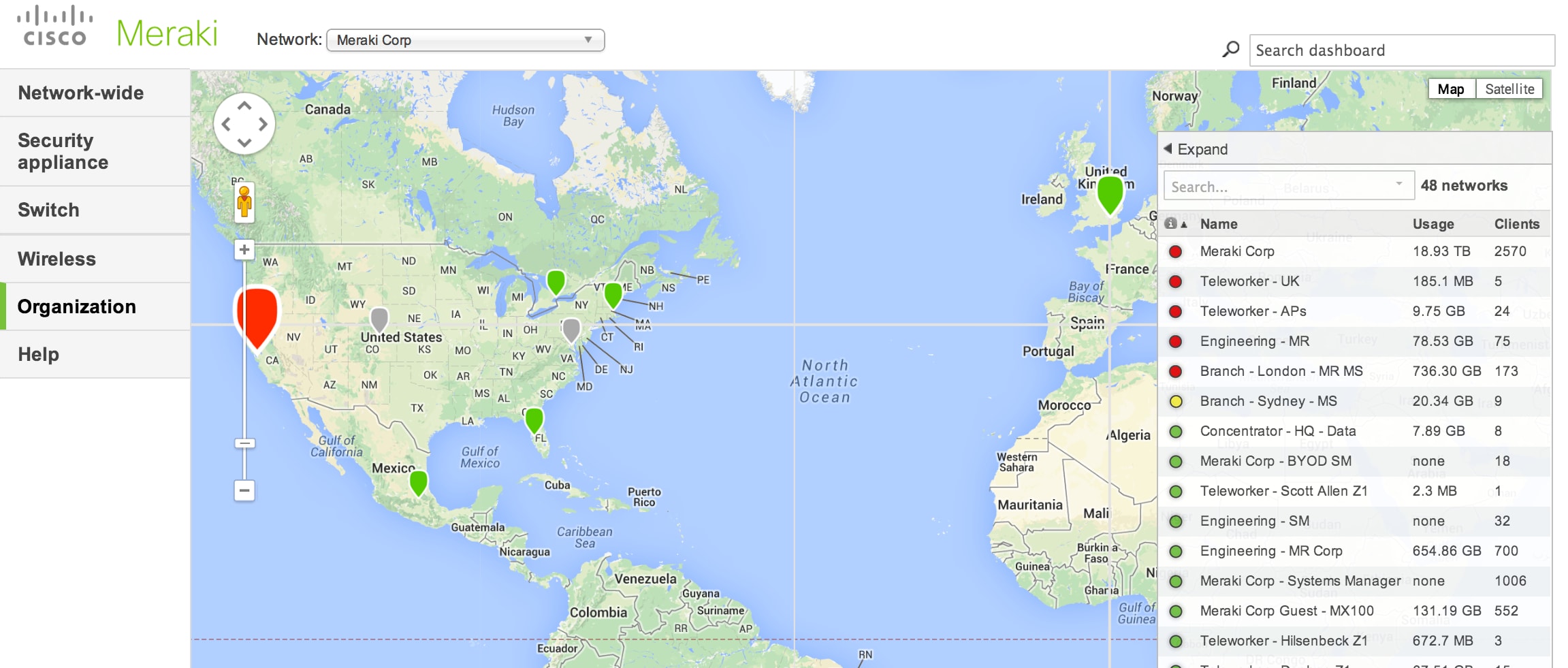
While it'due south simple to keep track of one AP, placing the device(due south) on a map in dashboard provides quick, high-level information on the health of the networks and of all the devices in your organization.
There are two different ways to visualize your deployed APs. The first is through the integrated Google Maps feature where APs can either be dragged and dropped onto the map (navigate to Monitor > Maps & floor plans and select Place APs on map). Or they can be placed by entering in the location'south address (navigate to Monitor > Access points, select the AP, and click on Edit configuration).
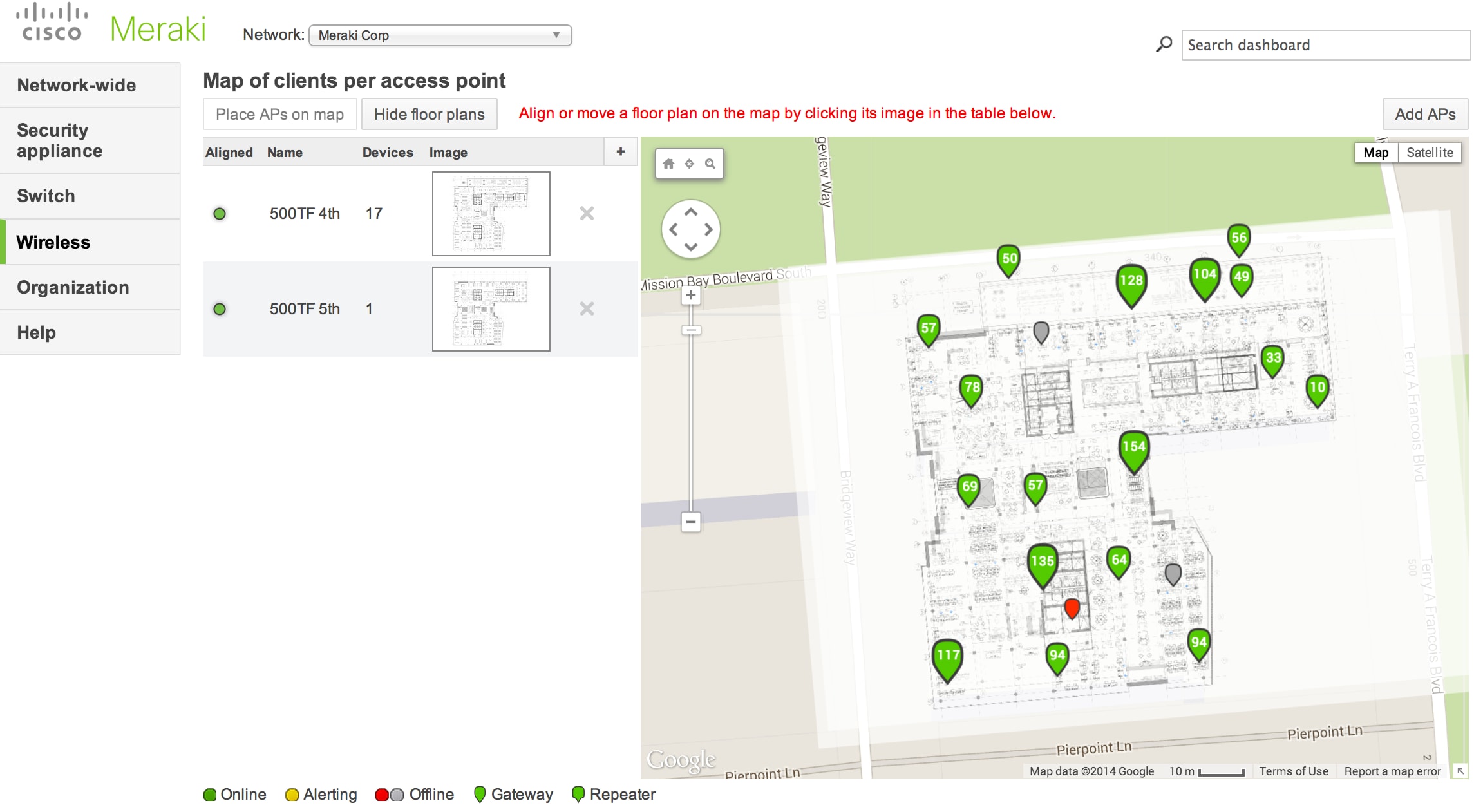
The second way is past uploading a custom map or floor plan that allows a more customized monitoring experience. This is done rapidly by navigating to Monitor > Maps & flooring plans and selecting Edit floor plans. Clicking the + that appears prompts the upload of a floor program file whose position will be overlaid on the map and can then be adapted to fit the physical location. Adding APs to the floor program is washed by selecting Place APs on map and dropping on the location.
Tagging and renaming APs
APs tin also be tagged by location or fifty-fifty renamed depending on needs. This is done on the Monitor > Access points folio. Tags are useful for grouping by building, broadcasted SSIDs, or floor. Just select any number of devices and choose the Tag drib down card. APs can either be assigned using existing tags or can be assigned a newly created tag. Past clicking into an AP from the same page and selecting Edit configuration, the AP can be renamed for easier management or reporting.
ESTABLISHING WIRELESS SETTINGS
Once a wireless network is up and running, it may exist desirable to implement additional custom configuration settings to meet your evolving needs. Creating SSIDs with authentication requirements, establishing firewall and traffic shaping rules, and assuasive discovery of devices like Apple tree TVs are but some of the settings that can exist implemented quickly and at any fourth dimension!
Creating SSIDs
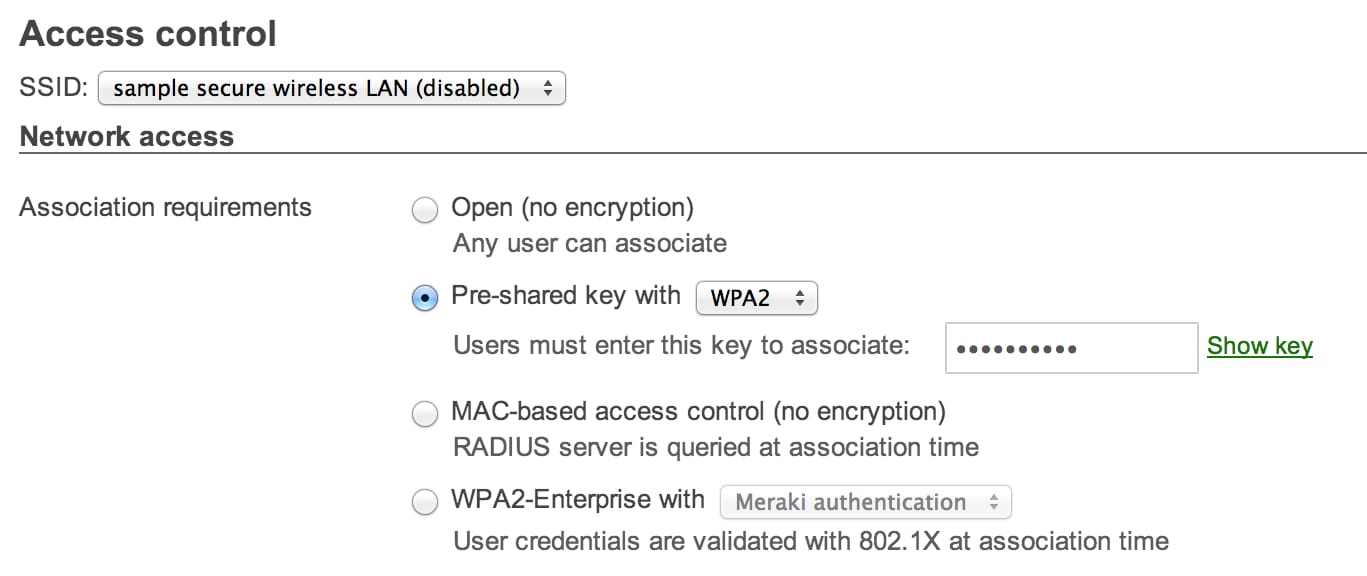
It's possible to configure upward to 15 SSIDs per network. The Configure > SSIDs page provides overview information, the ability to enable SSIDs, and renaming options. To enforce association requirements for each SSID, click on "Access control" on this folio or by going to Configure > Access control. Merely select from the available options: open, pre-shared key, MAC-based, or WPA2-Enterprise.
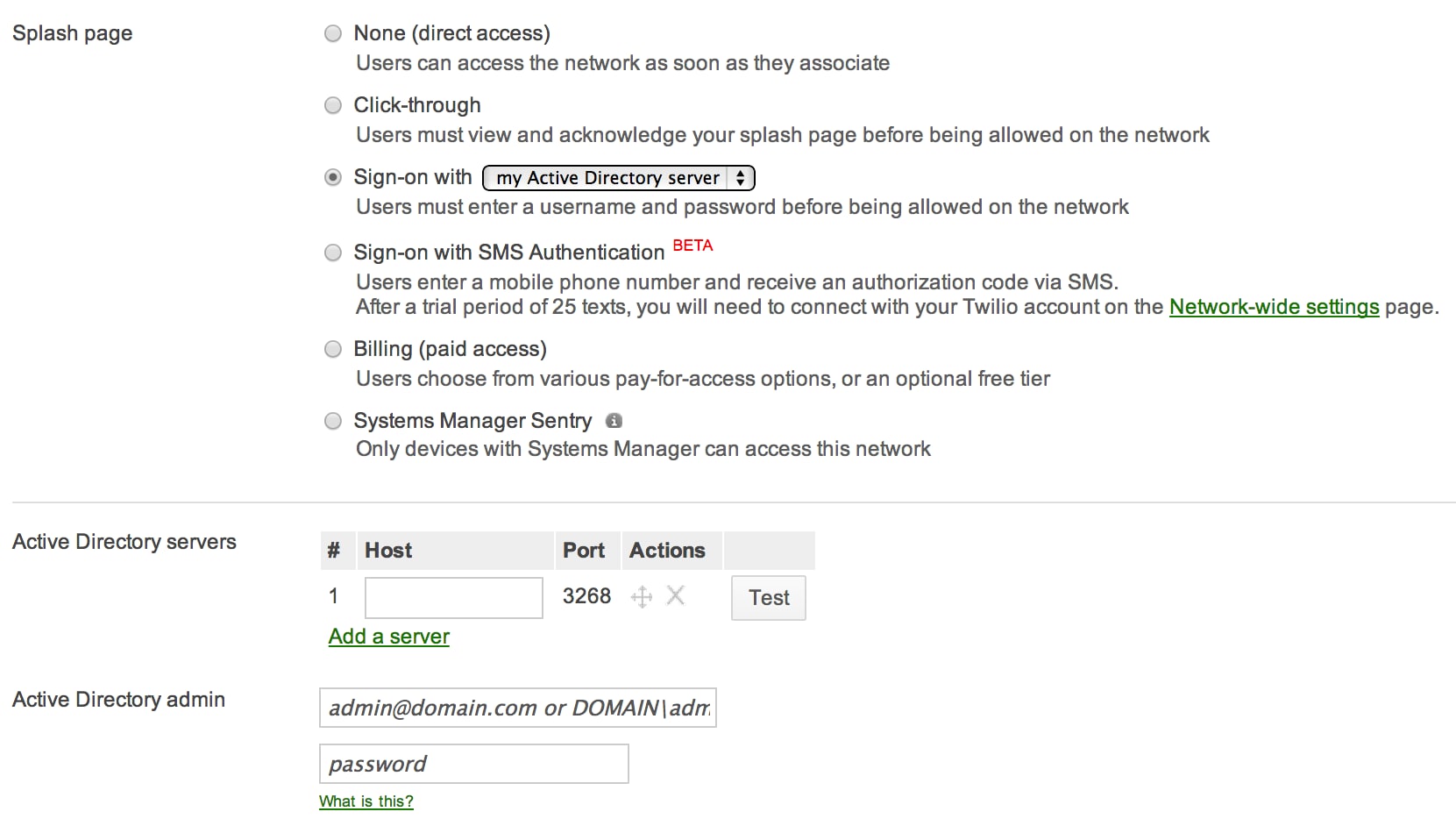
Active Directory authentication
Some other association option is to authenticate using an external Agile Directory server through a splash page. This is useful for preventing network access unless the provided sign-on credentials match those stored on the AD server. On the same Admission command page, choose Sign-on with and select my Active Directory server under the Splash pages section. In the newly populated Active Directory servers section on the page, click Add a server and add the IP address of the AD domain controller and relevant admin credentials. It is also possible to employ Active Directory as the RADIUS server in the WPA2-Enterprise setting.
Firewall & traffic shaping rules by SSID
At present that authorized clients have access to the wireless, establishing firewall and traffic shaping rules past SSID will allow, deny, or limit each client's use of network resource. The height section of the Configure > Firewall & traffic shaping page is dedicated to Layer 3 and Layer 7 firewalls rules. Hither, an admin can set certain rules for every request sent by a wireless user that volition exist evaluated from the height down, where the first rule to match will be applied. Simply enter the appropriate information in the Layer three section or choose the awarding blazon in the Layer 7 department.
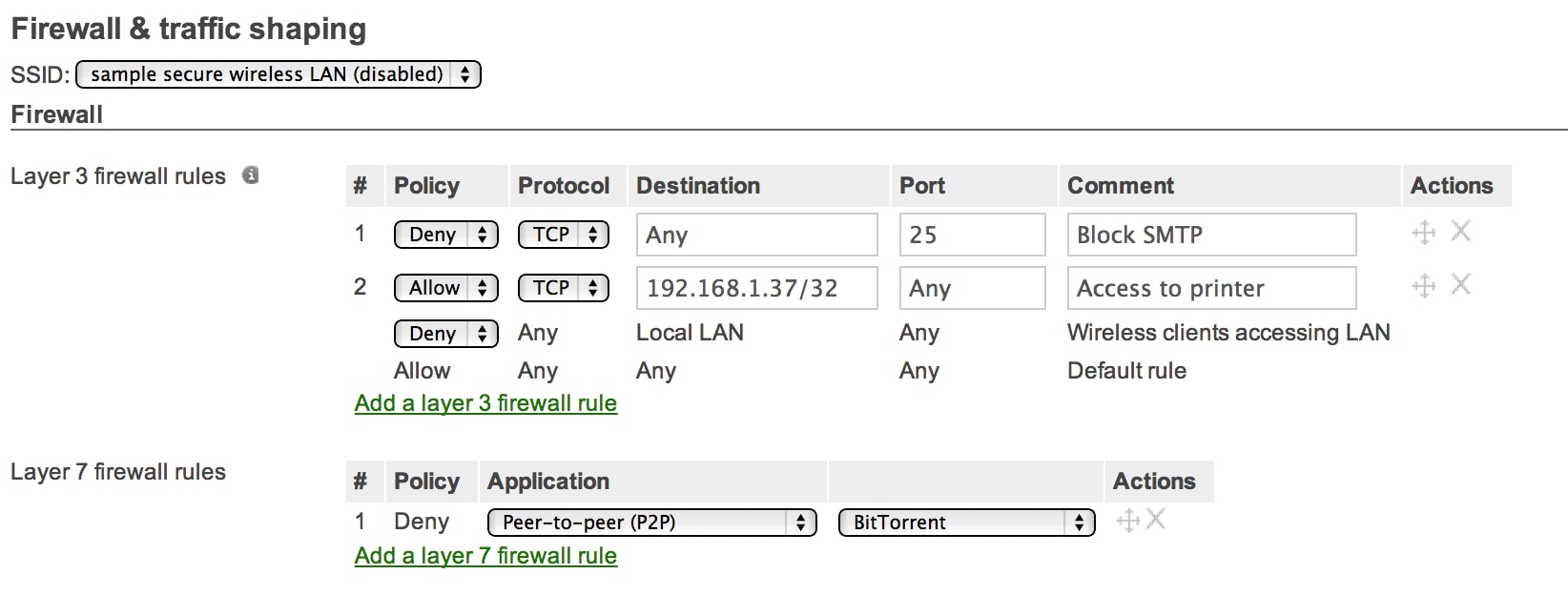
The second department of this folio allows the admin to set traffic shaping rules that limit per-client bandwidth usage or tin limit/open up usage by awarding. Cull Shape traffic on this SSID under the Shape traffic section, then click Create a new rule. In the Definition section click Add together + and cull the awarding groups or specific applications to bear upon, and then fix the Per-client bandwidth limit for those selected applications. Admins tin constitute numerous Layer 7 traffic shaping rules on each SSID.
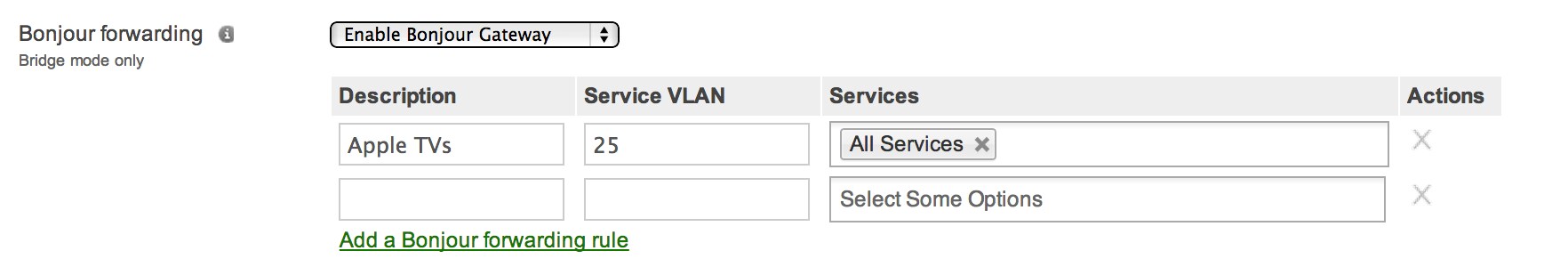
Enabling Bonjour forwarding for Apple TVs
Often other wireless devices, like Apple TVs, need access to the wireless network. Bonjour is used for automated discovery of Apple TVs on IP networks and, if on another subnet, needs to be permitted in dashboard. Cisco Meraki uses Bonjour forwarding to allow Bonjour advertisements to exist forwarded betwixt subnets. To enable, navigate to Configure > Access command and scroll to the Bonjour forwarding field nether Addressing and traffic. Choose Enable Bonjour forwarding and select Add a Bonjour forwarding rule to specify a particular service that the forwarding will be limited to, e.g. Apple TVs.
DON'T FORGET…
While this blog post covered the basics of getting your Cisco Meraki wireless network up and running, customization is by no ways limited to simply these topics. Explore your dashboard, browse the Cognition Base, check out our Product Documentation, or explore meraki.cisco.com for even more information and features.
Source: https://meraki.cisco.com/blog/2014/05/from-unboxing-to-configuring-settings-all-under-one-roof/
Post a Comment for "Make Meraki Run Dns Tests Again"